Cody Martin explains how to assess your mail security risk and develop standardized operating procedures for mail screening.
In this recorded workshop, RaySecur’s Director of Mail Security explains how to assess your mail security risk and develop standardized operating procedures for mail screening.
Implementing a mail security program is often the missing piece in a comprehensive physical security program.
In this 1-hour workshop, Cody Martin covered mail security risk & SOP in detail.
- Complete SOP Policy Statement
- Framework of a mail security SOP
- Deeper understanding of risk level & mail threats
Take the PDF with you ↓

About Cody Martin
Director of Mail Security
& SOP Team Lead
Cody Martin had over 12 years of experience as a Federal Agent with the U.S. Postal Inspection Service, and several additional years as a mail security consultant.
- USPIS Dangerous Mail Specialist & Instructor
- Co-created USPIS IED Program for National Headquarters
- Investigator on high-profile / VIP cases
- Screened mail for the NFL, NBA, President George W. Bush (ret.)
- First responder to hundreds of incidents
Mail-borne Threats
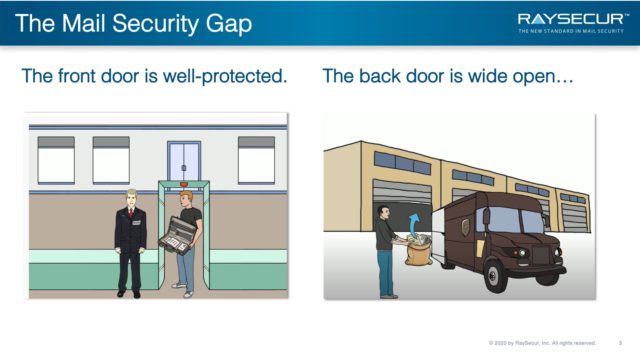
The Mail Security Gap
The front door of most corporate office buildings, data centers, financial institutions, or pharmaceutical manufacturers are well secured.
Security cameras, security checkpoints, identification protocols, controlled access points, etc., are all part of a physical security plan.
In contrast, the back door to the mailroom is often far less secure.
Someone can drop a letter or small package into an anonymous USPS collection box, which often enters through a back door or loading dock of a business bypassing all of those security measures.
These items then have an opportunity to make it straight up to the CEO’s office or to be delivered right to the heart of an organization’s critical infrastructure.
More common than you think.
1 in 3 Fortune 500 companies receive at least one mail threat per year.*
2019 Industry Mail Security Survey
- 34% of surveyed companies had at least one mail threat detected in the previous year
- 16% had more than 3 threats in that same time period
- Threatening letters doubled
- Drugs and illegal substances quadrupled
You can see by the numbers above, the odds of being targeting by a mail related threat are greater than you may think.
The big takeaway here is the increase in threatening letters, which has doubled over the last year, and the fact that drugs and illegal substances in the mail have quadrupled during the same time frame.
* Government Technology & Services Coalition, “Third of Companies Got Mail Threats in Past Year While Biological Screening Doubled,” May 19, 2019
10 incidents per day — that we know of
You may notice discrepancies in reported incident numbers.
Keep in mind that many incidents are not reported or are underreported based on agency requirements and classification standards.
RaySecur compiles and analyzes mail threat data on a regular basis. This info is published in our Mail Threat Data center.
USPIS 2019 Annual Report
- Dangerous Mail Investigations (DMI) Unit
- 400 specially-trained inspectors
3,289 suspicious incidents (powders, liquids) - 125,000 suspicious mail items subject to forensics exam
US Bomb Data Center
- 7,404 suspicious packages in 2018
- 2,261 incidents involving letters or parcels
What we do know is that the numbers are high and we are seeing large increases in certain areas.

Chain of Custody is Crucial
If you know the sender and there is an established chain of custody, there is a much lower likelihood of a mail-borne threat being contained in that mail piece.
Chain of custody may include an item’s vendor, supplier, manufacturer, etc.
Items that do not fit this description offer more opportunity for threats to be introduced.
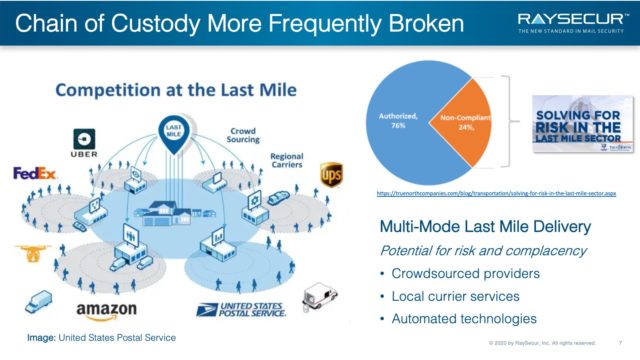
The "Last Mile" Security Problem
The “last mile” is simply the last leg of the delivery route, prior to a letter or parcel arriving at its final destination.
With more competition than ever in this arena, we are seeing the chain of custody more frequently broken.
Most people have seen this at their own residence in the last few years. It’s not unusual for deliveries to be made from personal vehicles, rental trucks, etc—and it’s never the same vehicle.
This allows more opportunity for the introduction of threats as well as it increases the need for more thorough screening.
Small is the new Scary.
The priority in mail screening has moved from identification to detection.
This is important because it has removed unnecessary steps from mail screeners and turned those over to external resources.
Screening has also moved from being concerned with large threats focusing on explosives, to the vastly more common threats found in small packages and letters (liquids, powders, etc).
Threats are overwhelmingly smaller in nature due to the anonymous nature of how these can be introduced into the mail stream.
This also facilitates a lack of chain of custody and no bill of lading.
One of the tools often used by US Postal Inspectors is a portable x-ray. Agents can easily identify dangerous items, explosives, contraband, etc.
However, when it came to powders, liquids, etc, identification becomes much harder. As first responders, US PIS Agents’ job is to screen up through identification through whatever means necessary.
But for mail screener, the level of engagement is much lower. At this level, companies should focus on detection. Once a potential threat is detected, it’s time to contact external resources.
Spending time on identification is unnecessary at this point in the process—leave that to the professionals.
Physical & Cybersecurity Overlap
Warshipping is when a small, computerized device is mailed to your organization with the intent to gain entrance to your network or other sensitive information.
Using a cheap computer, which draws minimal power, this technique bypasses your physical security measures by entering your organization through the mail stream or back door.
Mitigate by processing mail quickly, scanning for anomalies, and discarding packaging.
Worst-Case Initial Response
When first responders get a callout regarding a mail-borne threat, their response is going to be based on a worst-case scenario.
A false positive or mail threat hoax will receive the same initial response as a legitimate biological threat. As a result of this, most responses are very disruptive to an organization, which is typically the goal of the suspect.
This is something to keep in mind as you are developing methods to mitigate mail threats: how are you going to interact with first responders and what will that look like?
Mail Security Operations Post-COVID
What is "normal" now?
The “new normal” is not permanent. However, some of these aspects such as certain cleaning requirements, testing for illness, etc., may remain in our workplaces.
This guide focuses on two scenarios, with two conditions.
These are, in general, what we are seeing when we talk to our clients across multiple industries:
A) Skeleton Crew
An organization has been partially closed and has been running on a skeleton staff. This has been most of our clients since about two weeks after the pandemic started.
Organizations sent the entire staff to work remotely and if they didn’t think about it ahead of time realized that mailroom employees are essential.
B) Fully Shuttered
Organizations that fully shuttered and are now facing the difficulties of restarting all functions and processes.
There are some unique problems this situation creates due to a massive backlog of services that have to play catch up.
The two base conditions we will apply to the now-standard organizational scenarios:
- Social distancing protocols are in place.
- Assumption that there is no reduction in screening for security purposes
Start with OSHA Guidance
OSHA sets the minimum safety standards for the workplace and is generally accepted without question.
As an organization, OSHA puts the employee and the workplace in the middle of the decision-making process.
Although sometimes painful in the workplace, there is a reason for the guidance.
Workplace Safety
OSHA identifies risk and provides steps to reduce it in the workplace.
And they provide a methodology for Engineering and Administrative Controls that will drive an organization’s Personal Protective Equipment (PPE) requirements.
Companies may leverage different guidelines and mail security protocols for Executive Protection teams.
Adjusting to the New Normal
Before Covid, most organizations had zero controls on particle transmission between workers.
- Contamination control methods were not a concern.
- Basic cleaning procedures were generally “good enough.”
- PPE requirements were recommended but optional and, in most locations, rarely used.
Every organization and site will require individualized adjustments in order to fully reopen mailrooms during or after a Covid shutdown.
As of now, the “new normal” is PPE and distancing. Even when the major Covid concern is over, organizations should be prepared to reinstate these safety measures, in the event of another pandemic.
The balance between employee safety and Mail Center functionality is key and must be understood by management and executed by the mail center staff.
Designated workspaces and surfaces are critical to practicing safe mail center operations. It makes it easier to maintain contamination control methods and minimize the threat of spreading things around.
Working in designated teams supports everything from contact tracing to minimizing the impact on the organization if exposure occurs.
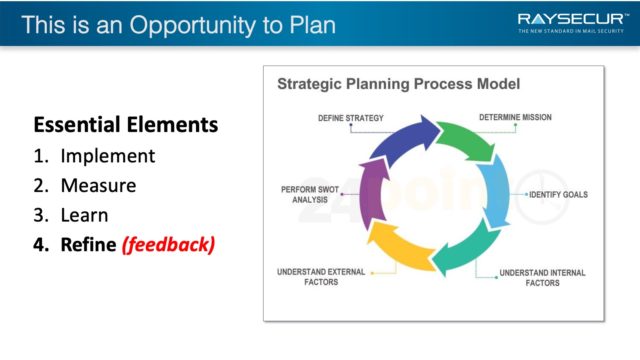
Opportunity to Plan
No matter what model you decide on, generally two things must be present for it to be successful.
First, it needs to have a re-evaluation or review step to ensure the process is validated. We need to measure what we are doing.
The second involves feedback, if there is no feedback loop included in the process critical information is being missed and we can’t refine what we are doing.
This is an ongoing process and should be constantly reinforced within the organization.
If some of the measures or processes you are using are not working, they should be identified and changed. Then we start the process over again.
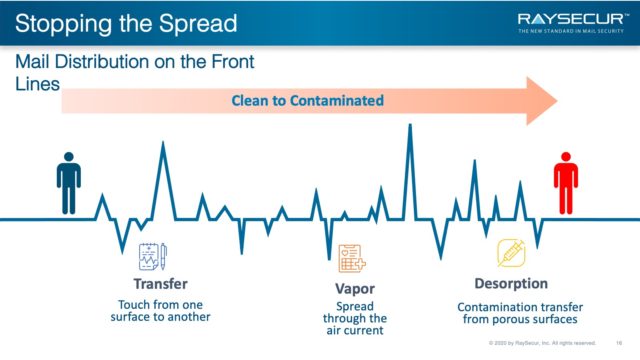
Stopping the Spread
Many of these recommendations are the same as general best practices we’ve all been hearing since March.
- Relocate workspaces and create dedicated areas to promote employee distancing.
- Prepare a mail reception site to support easy decontamination and quick preparation for reuse with the next process if needed.
- Install shielding when 6-foot distancing cannot be maintained.
- Utilize of Personal Protective Equipment (PPE) while screening.
- Assigning work areas with boundaries between them and “drop points” where employees can transfer packages between themselves while maintaining social distancing.
- Add handwashing/sanitizing stations in each independent work area (as opposed to communally).
- Increase the number of dedicated wash stations.
- Conduct meetings remotely, even when all involved are at the same location.
- Change gloves frequently, and wash hands when processing mail.
The 6-Foot Rule
Standard best practices apply to the 6-foot rule: lock boxes, plexiglass, and managing the flow of mail and personnel.
Doors can be kept open with a plexiglass divider, barring entry but promoting airflow—rather than closed door with an attendee.
This leads to 2 benefits:
- Vendors do not bring in packages
- All deliveries are now coming through the mail center and can be scanned
A Method for Change
No matter what, part of this effort has to happen now it has to happen as a team. Regardless of what your organization looks like in the spectrum, everyone involved has a role.
Management’s Key Roles
Providing guidance and be prepared to answer questions about that guidance. Many good ideas have a tendency to bubble up from where most of the work gets done.
As problems are worked through and new ideas are implemented, guidance needs to be updated to support the team.
Management needs to manage and support teams as they need not necessarily with what they want. Very few people get up in the morning with the intent to wreck the office today.
The individuals buy into the team, the team buys into the organization, and collectively efforts steadily improve the situation for all.
Most likely some of the guidance will frustrate both the mail center and those that depend on it.
For example, if management has designated pick up hours or shortened the pick-up times to allow for cleaning or other mandated tasks; not enforcing those timelines quickly hurts the team.
Mailroom Teams’ Key Roles
As tasks are increasingly separated combined with the required physical separation between people, we are seeing efficiency decrease.
Historically, individual tasks now become team functions unless all tools are repeated at all workstations.
Following established protocols is critical for not only individual safety but that of the entire organization.
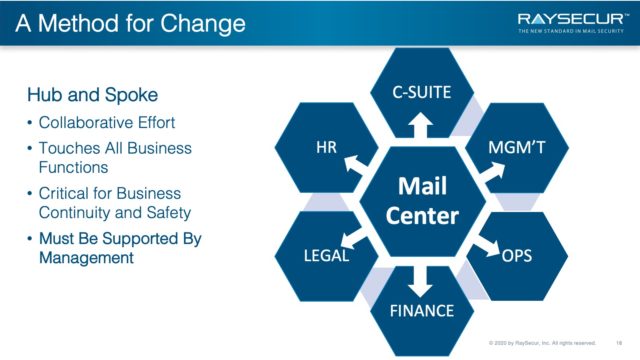
Thinking of the mailroom like a hub and spoke logistical effort a couple of facts become clear.
There is not a single part of the organization that the mailroom will not “touch” and that goes both directions upstream and downstream.
Managing Backlog
Active management of techniques and processes is critical to success. There may be a lot of mail.
To make things worse, the mail backlog may increase as people come back to work and activities come back online. Or it may increase if and when more stringent lockdowns are enforced.
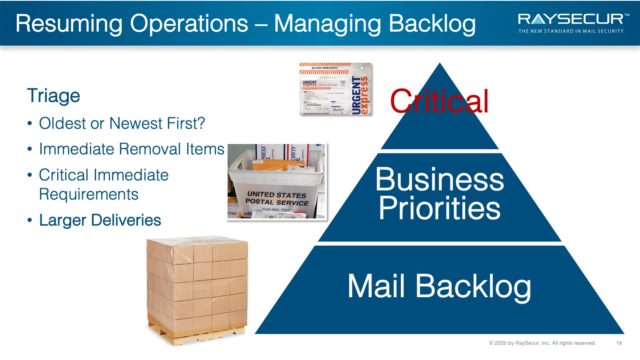
Pick a point in time to start your mail workflow screening, starting with either:
- Oldest unscreened mail
- Newest unscreened mail
- Title or department
Plan for increased logistical requirements—boxes may become pallets and require increased material handling equipment.
Immediately remove mailers and media mail from delivery and screen and remove all non-essential mail.
Adjust memorandums of understanding on destruction authorization about personal mail
Inform employees that personal mail is not a priority at the moment.
Prepare a mail reception area, so mail can be deposited and not cross paths with others.
Shared workstations should have all necessities to manage workflow, including PPE and sanitation considerations.
Understanding PPE for Mail Handlers
Industrial-style N95 masks have a bypass valve. This means that a user’s breath bypasses the mask’s filter when they exhale.
The mask offers some protection to the user, but not the others around them.
Surgical/disposable masks are the standard in healthcare for good reason—and they are generally recommended for most users.
In all cases, handwashing is crucial. And mail is dirty. Even without Covid protocols, mail handlers should wear gloves.
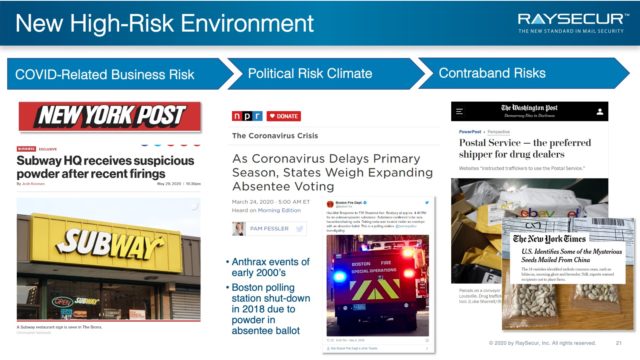
New High-Risk Environment
Mail threats are on the rise for many reasons. Much of this mail threat increase is due to social and financial frustrations.
Most mail threats are sent by people well known by the targets.
There are countless examples of how stressors and the real world interact. Human beings are all different and some act out when an individual’s sensitivities are touched uncomfortably.
- Insider threats
- Layoffs
- HR departments
In June of 2020, the Subway Sandwiches corporate HQ received a mail threat after a large round of layoffs.
Mail Security in Covid Environment
The risks are not the same for everyone. Your level of risk from mail-borne threat varies widely, based on your organization’s makeup.
DHS Risk Factors
The Department of Homeland Security and Interagency Security Committee identify some of the risk factors for mail-borne threats.
Industry
About a dozen industries are more likely to receive threats. The list includes including banking, legal, energy, military/industrial, and transportation—among several others.
Symbolism
Is the organization well-known and controversial? Twitter, Fox News, the NRA, or Planned Parenthood, for example, may be more likely targets than a lower-profile organization.
Location
Organizations in large, multi-tenant facilities and urban centers are at higher risk.
This especially true for organizations in symbolic areas: Washington DC and New York City, for example.
Portland, OR has been in the news a lot lately. This was true of Ferguson, MO and Charlottesville, VA for a time.
Size
Organizations with large employee counts are more likely to be targets. This is just a matter of scale and statistical likelihood.
Mail Volume
Similar to company size, the larger the volume of mail stream at a company, the higher their risk, simply due to scale.
Given the rising number of mail-borne threats, all organizations should have a mailroom security program in place.
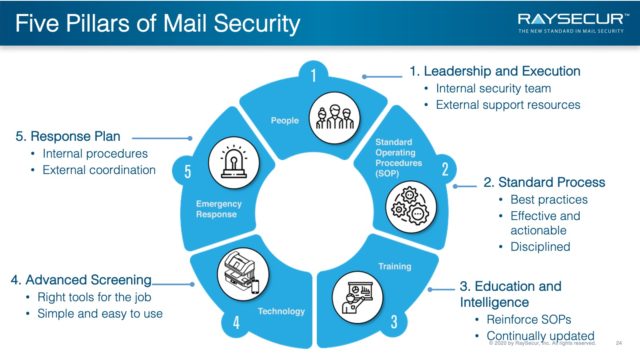
A robust, comprehensive mail security program is built on 5 independent pillars:
- People
- Standard Operating Procedures (SOPs)
- Training
- Technology
- Emergency Response
Pillar #1: People
Having the right people begins at the top. A company’s executives must be committed to providing the resources for an effective mail security program.
The focus on people must include everyone from the front-line worker to the top-level executive, and outside, third-party resources.
Executives must provide needed resources. Screeners on the frontlines should understand their importance in the mail security process.
Everyone is part of the solution.
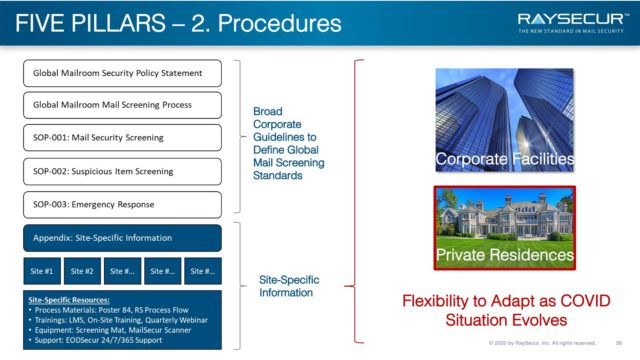
Pillar #2: Procedures
Standard Operating Procedures are critical in dealing with mail-borne threats.
- Help set policy
- Set standards and training
- Establish screening processes
- Provide guidelines suspicious item screening
To effectively deal with mail-borne threats, companies must systematize their processes with Standard Operating Procedures (SOPs) — and then adhere to them.
Pillar #3: Training
Ongoing mail security training, education, and coaching are key when it comes to implementing mail screening procedures and ensuring proper use of screening technologies.
Well-trained personnel is key to mitigating mail-borne threats. Not only will efficiency increase, but an experienced mail screener is more likely to see something out of the norm.
They are also able to more easily recognize trusted senders to expedite screening and have a better understanding of emergency procedures.
At a minimum, all mail handlers should be trained in the fundamentals of mail security covering the types of mail threats, identification of suspicious items, and the basics of visual and tactile inspection.
Operators of mail security screening technology should be trained in all aspects of their particular screening technology operation and threat detection.
Pillar 4: Technology
Mailroom security technology typically falls into two major types: those that can detect threats and those that can identify them.
Mail screeners need not be on the same level as law enforcement, in which they would identify each threat and its associated risk.
Instead, screeners need only detect a threat. Once a threat is detected, screeners would follow SOPs, and the threat will be handled accordingly.
Therefore, technology should be introduced as a way detect threats, not necessarily identify or explain them.
Pillar #5: Emergency Response Plans
If your organization does not have an emergency response plan in place, you should strongly consider creating one immediately.
These documents mandate how a threat is managed, and guide the actions of those involved.
Most organizations use a two-tiered approach when handling emergency response requirements.
They have both Emergency Response Plans (ERP) that mandate how the entire threat is managed and Emergency Action Plans (EAP) that dictate the actions of those involved.
These plans need to be prepared and rehearsed. All individuals required for their implementation must be involved to ensure success.
Additional Resources
US & UK Guidelines
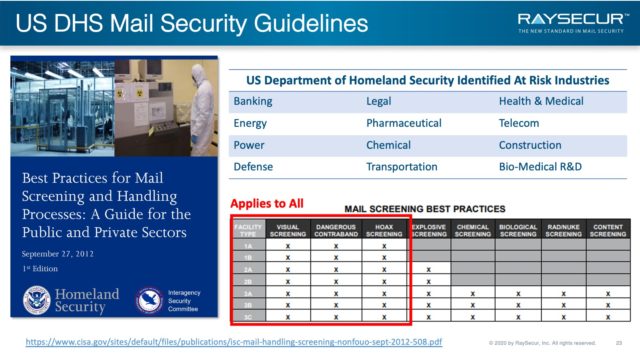
RaySecur recommends mailroom and security personnel review the guide put out by US DHS, Best Practices for Safe Mail Handling.
The DHS guide discusses risk assessment of the facilities and mail handling operations, and best practice to minimize risk and exposure to personnel and the public.
For further documentation, the UK CPNI Guidelines, known as PAS 97, are an excellent resource.
The PAS 97 specifies measures to assist businesses and other organizations in identifying and minimizing the impact of items of mail that represent a threat, or could otherwise cause concern or disruption.
Classification & requirements
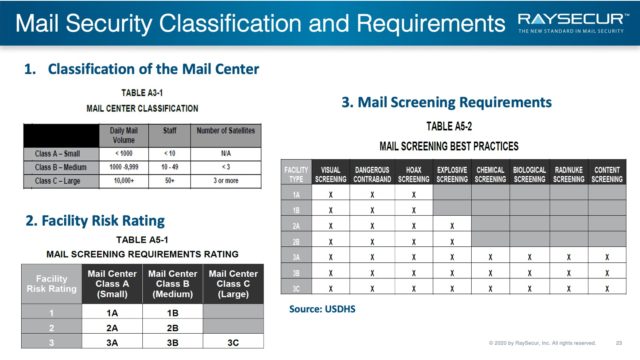
The US DHS provides several helpful tables to help organization rate their own risk, and begin to plan their mail security protocols.
Size & scope
Table A3-1 will help determine the size of your mail center, in relation to other organizations’ mail centers.
Facility risk level
As seen in previous slides, organizations can be rated high risk 1, medium 2, or low risk 3.
By cross referencing the size of center A,B,C with level of risk 1,2,3 will give you the requirement rating, found in table A5-1.
What to screen for
Table A5-2 will provide a guide to help determine what your facility should screen for.
This is an excellent guide to start discussing with your team how to best implement a mail center security process.
Safe mail handling
This slide highlights a few resources organizations should reference during mail security program implementation.
The first is Poster 84, which annotates common characteristics to look for in relation to suspicious mail or packages.
The second is the guide put out by DHS, Best Practices for Safe Mail Handling.
What’s next?
Refining a mail security program in a Covid pandemic environment is a unique challenge.
It is unfamiliar to many and may present issues to those who are new to the world of mail security.
RaySecur can help implement a sound mail center security practice and bridge the gap in your facility’s physical security.